Microsoft and U.S. Authorities Disrupt North Korean AI-Driven Remote Work Scam
Microsoft has shut down 3,000 Outlook and Hotmail email accounts linked to North Korean IT workers posing as remote freelancers in order to infiltrate U.S. and international companies. These operatives, often using fake or stolen identities, were part of a state-backed scheme to generate millions of dollars for the North Korean regime in violation of international sanctions.
According to Microsoft and U.S. authorities, the workers used AI-powered tools like FaceSwap to alter profile images for job applications. They also began experimenting with voice-changing technology, a step that could eventually remove the need for human facilitators in fake identity creation.


The FBI, DOJ, and other agencies also dismantled 29 ‘laptop farms’ across 16 U.S. states. In these setups, unwitting accomplices or hired facilitators kept computers that the North Korean workers could access remotely, making it appear they were based in the country. One of these facilitators was a U.S. military service member.
Cryptocurrency tracing by ZachXBT revealed that since January 2025, North Korean IT workers have received over $16.5 million in crypto payments, averaging nearly $3 million per month. Typical individual payments ranged from $3,000 to $8,000 monthly, indicating the scheme could be running between 345 and 920 job roles at the same time.
This crackdown highlights the growing sophistication of North Korean cyber-enabled revenue generation. By blending IT outsourcing fraud with AI, crypto laundering, and global identity theft they’ve been able to bypass sanctions.
McHire Breach: Weak Password in McDonald’s AI Hiring Tool Exposed Applicant Data
McDonald’s AI-powered hiring platform McHire, created and operated by Paradox.ai, recently suffered a serious security flaw that exposed sensitive job applicant information. The issue was discovered by security researchers Ian Carroll and Sam Curry, who found that the platform’s administrative portal could be accessed using extremely weak default credentials, username: 123456 and password: 123456. This basic oversight immediately granted full administrative privileges over the system.
Once logged in, the researchers identified an insecure direct object reference (IDOR) vulnerability in one of the platform’s API endpoints. By simply changing numerical applicant IDs in the request, they could access data belonging to other applicants without any authentication checks. This flaw potentially allowed unauthorised users to browse through personal details of millions of job seekers without restriction.
The AI chatbot at the centre of the hiring process, named Olivia, is designed to guide applicants through job applications and screening questions. However, due to the vulnerabilities, anyone exploiting the flaw could view the data collected by Olivia. This includes names, email addresses, phone numbers, shift preferences, personality test responses, and even applicant session tokens. Early estimates suggested that up to 64 million job seekers worldwide might have been exposed.
Paradox.ai’s own investigation, however, determined that only seven chat records were accessed during the researchers’ testing, with five containing personal information. They found no evidence of broader exploitation, no signs of data exfiltration, and no indication that malicious actors had discovered the vulnerability before it was responsibly reported.
The flaw was disclosed to Paradox.ai on June 30, 2025. Within hours, the company disabled the default administrative credentials, closed the insecure API endpoint, and implemented a patch. The vulnerability was fully resolved by July 1.
In a public statement, Paradox.ai accepted responsibility for the incident, apologised for the oversight, and announced the launch of a bug bounty program to incentivise ethical reporting of security issues. While stating that the issue originated with its third-party vendor, McDonald’s expressed disappointment in the lapse and reaffirmed its commitment to ensuring that the personal information of job applicants remains secure.
This incident underscores the critical importance of basic cyber security hygiene in AI-driven business tools. Weak authentication practices, default credentials, and missing authorisation checks can undermine otherwise sophisticated platforms. This puts both brand reputation and customer trust at risk. Even advanced AI applications must adhere to strict security protocols to prevent large-scale data exposure.
NASCAR Breach Exposes Fans’ SSNs and Operational Data via Medusa Ransomware Attack”
In April 2025, the Medusa ransomware group infiltrated NASCAR’s IT network and demanded a $4 million ransom. The group even listed NASCAR on its leak site, posting screenshots of internal raceway maps, staff email addresses, names, job titles, and credential-related documents, signalling a substantial operational data breach.
Investigators confirmed that the intrusion occurred between March 31 and April 3, 2025, with the incident officially discovered at the beginning of April. NASCAR promptly activated its incident response plan, secured its systems, engaged a cyber security firm for investigation, and informed law enforcement. While NASCAR initially refrained from confirming the attackers’ identity, subsequent investigations confirmed that the exfiltrated files included personally identifiable information (PII), including names and Social Security numbers.
Affected individuals began receiving breach notification letters on July 24, and NASCAR is offering them one year of free credit and identity monitoring via Experian, along with a toll-free support line for inquiries. Despite multiple requests, NASCAR has not disclosed the total number of individuals affected, nor confirmed whether the ransom was paid or if any of the stolen data was publicly released. This breach aligns with a broader FBI and CISA warning that highlighted Medusa as one of the most active ransomware-as-a-service (RaaS) groups, responsible for over 300 attacks on critical infrastructure worldwide.
Allianz Life Customers Impacted by LockBit Ransomware Attack on Third-Party Vendor
Allianz Life Insurance Company of North America, a major U.S. insurer, has confirmed a data breach stemming from the 2023 cyber attack on one of its third-party service providers. Infosys McCamish Systems (IMS), which offers insurance and annuity administration services, was compromised in November 2023 when attackers deployed the LockBit ransomware, disrupting operations for months and affecting multiple IMS clients.
Following forensic investigation, Allianz Life revealed that the breach exposed sensitive personal information belonging to certain policyholders. The compromised data may have included names, Social Security numbers, policy and account numbers, dates of birth, and financial details related to insurance policies. Although Allianz stated there is no evidence the stolen information has yet been misused, the exposure poses a long-term risk for identity theft and fraud.
According to Allianz, the breach occurred at IMS’s systems, not Allianz’s own infrastructure, but it still affected Allianz customers whose information was stored or processed by IMS. Once informed of the incident, Allianz initiated a review of the affected data, confirmed the identities of impacted individuals, and began issuing individual notification letters in accordance with U.S. state data breach laws.
The company is offering two years of complimentary identity theft protection and credit monitoring services through a leading cyber security provider to those affected. Allianz also said it is working closely with IMS to ensure additional security enhancements are in place to prevent a repeat incident. These include stricter vendor security audits and improved encryption practices for stored and transmitted data.
This breach is part of the wider fallout from the LockBit ransomware attack on IMS, which reportedly impacted over 2.5 million people across multiple insurance companies and financial institutions. The LockBit group, one of the most active ransomware gangs globally, is known for its double-extortion tactics, stealing sensitive data before encrypting it, and then threatening to leak it if the ransom is not paid.
The Allianz incident underscores the growing supply chain risk in the insurance sector, where cyber criminals increasingly target service providers handling large volumes of sensitive financial and personal information. As Allianz’s case shows, even companies with robust internal cyber security can be affected when a third-party partner is compromised.
ToolShell: Widespread SharePoint Zero-Day Exploit Breaches 400+ Government & Utility Systems
In July 2025, a critical zero-day vulnerability, nicknamed “ToolShell”, was exploited to breach on-premises Microsoft SharePoint servers, triggering a global wave of cyber intrusions. Initially detected around July 7, the attack gained momentum in subsequent waves, culminating in at least 400 confirmed compromises spanning government agencies, utility operators, and private organisations.
Among the confirmed victims were high-profile U.S. federal agencies including the Departments of Energy, Homeland Security, Health and Human Services, as well as the National Nuclear Security Administration. The California Independent System Operator, which oversees a significant portion of California’s power grid, was also impacted.
Attackers leveraged two critical flaws, CVE-2025-53770, enabling remote code execution, and CVE-2025-53771, permitting security bypasses, both of which circumvented Microsoft’s earlier patches for related vulnerabilities. These flaws allowed threat actors to:
Bypass multi-factor authentication and single sign-on.
Deploy malicious payloads.
Steal cryptographic MachineKey material.
Maintain persistent access even post-patching.
Multiple cyber threat groups, tied to China, were implicated in the attacks:
Linen Typhoon, linked to intellectual property theft.
Violet Typhoon, active in espionage
Storm-2603, deploying Warlock ransomware as early as July 18 and attempting cryptographic key theft to sustain long-term access.
In response, CISA and Microsoft issued emergency warnings, added the vulnerabilities to their Known Exploited Vulnerabilities catalogues, and released patches for supported SharePoint versions. However, experts warn that patching alone may not sufficiently dislodge attackers, due to the persistent access made possible through stolen keys.
https://cyberscoop.com/microsoft-sharepoint-attacks-400-victims-us-agencies/
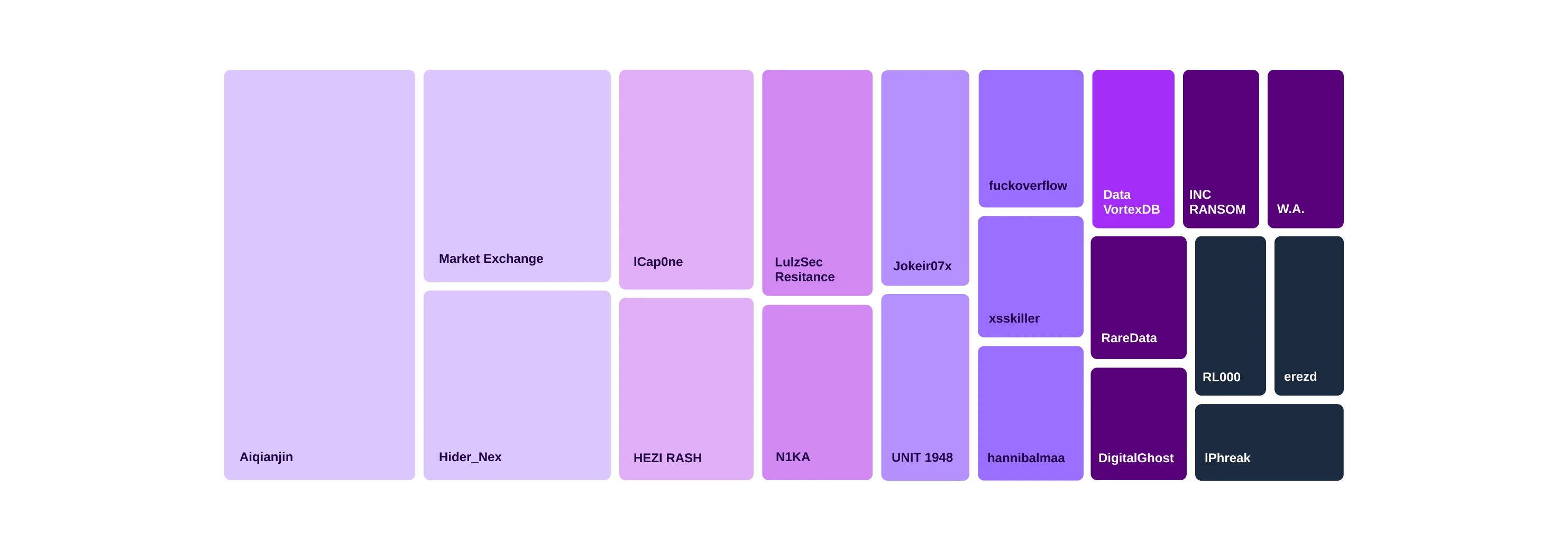
Threat actors targeting financial entities in July 2025
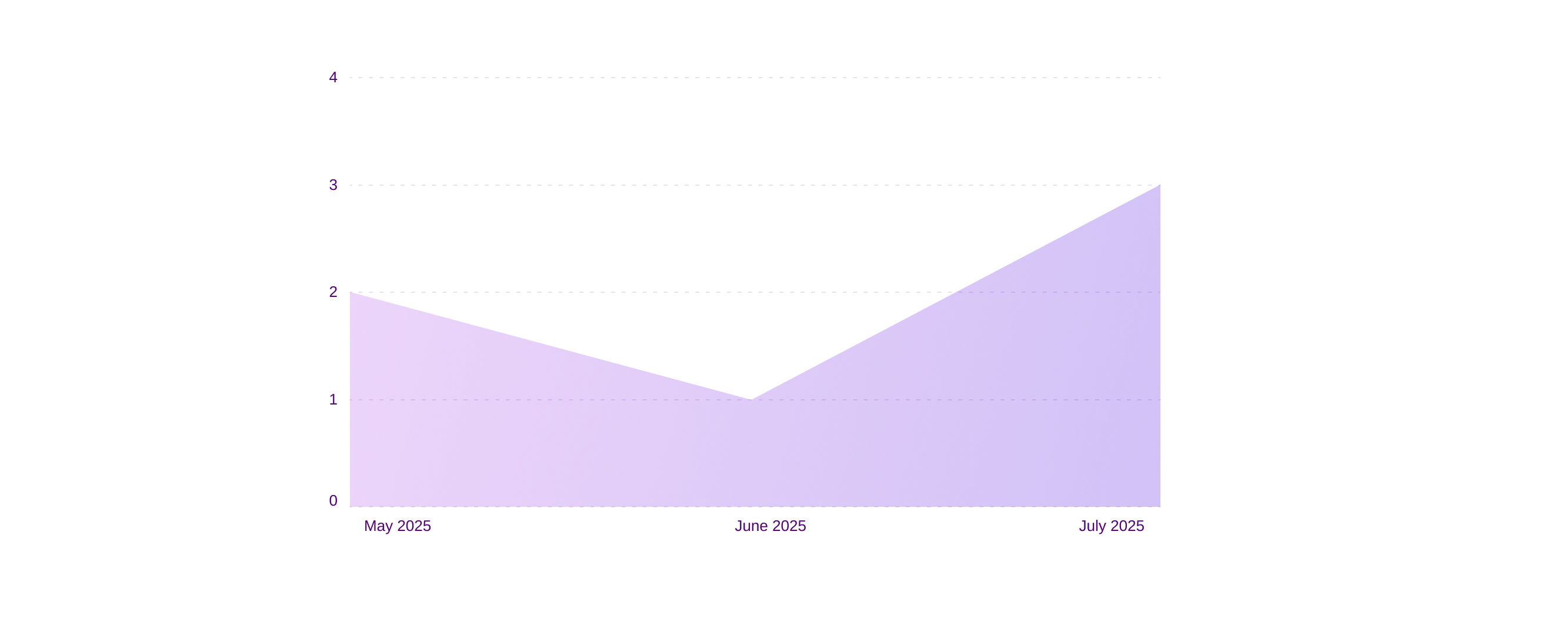
Ransomware vs Finance (last three months)

