ClickFix Campaign Uses Fake Booking.com Emails to Deploy Malware on Windows Systems
Cofense Intelligence has identified a growing phishing campaign named ClickFix, which impersonates Booking.com in order to deliver malware to users in the hospitality sector. Active since November 2024 and peaking in March 2025, these attacks use deceptive emails containing links to fake CAPTCHA websites that appear legitimate but are actually malware traps.
The scam tricks Windows users into executing keyboard commands that run malicious scripts. These scripts often deploy XWorm RAT (a remote access tool), Pure Logs Stealer, or DanaBot, targeting sensitive data and system access. In many cases, these attacks combine both remote access tools and data stealers.


ClickFix stands out for getting users to activate malware themselves through social engineering, without needing to download a file. Cofense warns that although Booking.com is the main brand impersonated, similar tactics are being used with spoofed Cloudflare and cookie consent banners. Only Windows users are targeted, those on other systems see a message saying the site only works on Windows.
The campaign highlights the growing sophistication of phishing threats and the need for heightened awareness, especially when prompted to run commands or interact with "verification" popups from seemingly trustworthy sources.
https://hackread.com/clickfix-email-scam-fake-booking-com-emails-malware/
UNC6040 Hackers Use Fake IT Support Calls to Infiltrate Salesforce and Corporate Systems
Google's Threat Intelligence Group (GTIG) has exposed a voice phishing (vishing) campaign by a financially motivated group known as UNC6040. These attackers impersonate internal IT support over the phone to trick employees, mostly in English-speaking divisions of global companies, into granting access to corporate tools, especially Salesforce.
The scam works by convincing employees to approve maliciously modified connected apps. These are often disguised as Salesforce’s legitimate Data Loader tool or rebranded as something innocuous like “My Ticket Portal.” Once attackers gain access, they extract company data in phases to avoid detection, often starting with small queries and later expanding to large-scale exfiltration.
In many cases, the stolen data isn't immediately used for extortion. Instead, weeks or even months pass before threats arrive, sometimes under the alias of ShinyHunters, to maximize psychological pressure. This delay complicates forensic investigations and response efforts.
UNC6040’s operations don’t stop at Salesforce. Once inside, they laterally move to platforms like Okta and Microsoft 365, expanding their control and harvesting additional sensitive data.
Prevention Tips (from Google GTIG):
Restrict tool access: Limit use of powerful tools like Data Loader to essential users.
Control app integrations: Ensure any new connected apps are vetted and approved.
Use IP restrictions: Enforce login and app access only from trusted IP ranges.
Monitor actively: Deploy tools like Salesforce Shield to detect abnormal data exports.
Strengthen MFA and training: Combine technical defences with employee awareness to detect and stop phishing calls.
This campaign underscores the danger of social engineering and the importance of user education alongside robust technical controls.
https://hackread.com/hackers-fake-it-support-calls-breach-systems-google/
Scattered Spider Shifts Focus to U.S. Insurance Sector Using Help Desk Social Engineering
Google’s Threat Intelligence Group has issued a warning that the cybercriminal group Scattered Spider, previously known for disrupting major UK retailers, is now actively targeting U.S. insurance companies. The group is using familiar social engineering techniques to exploit help desks and gain unauthorised access to internal systems.
Rather than using malware or exploiting software vulnerabilities, Scattered Spider impersonates employees or contractors in phone-based schemes. They convince support staff to reset passwords or share access credentials, making human error their primary entry point.
Two potential victims include Erie Insurance, which disclosed a breach on June 7, and Scania’s insurance division, both aligning with the timing of the new wave of attacks. While Google hasn't confirmed direct attribution, the pattern fits Scattered Spider's known tactics.
Why Insurers?
Insurers manage vast amounts of sensitive personal and financial data and operate complex customer service environments, ideal conditions for social engineering attacks. Fast-paced help desks often deal with urgent access requests, which can lead to lapses in verification.
Mitigation Recommendations:
Strengthen identity verification procedures for help desk interactions.
Train support staff to recognise impersonation attempts.
Enforce role-based access controls and permission limits.
Use multi-step verification for password resets and account changes.
Scattered Spider’s continued success shows that targeted social engineering remains one of the most persistent and effective cyber attack methods, especially in industries with high-value data and human-facing support operations.
https://hackread.com/scattered-spider-us-insurers-uk-retail-hit-google/
Hackers Abuse Google URLs to Deliver Stealthy Checkout Malware via Browsers
Security researchers have uncovered a sophisticated browser-based malware campaign that uses legitimate-looking Google.com URLs to bypass antivirus software and silently infect users during online checkout processes.
The attack leverages a trusted Google OAuth URL (https://accounts.google.com/o/oauth2/revoke) embedded within compromised Magento-based e-commerce sites. A manipulated callback parameter in the URL decodes and executes obfuscated JavaScript using eval(atob(...)), effectively hiding the malware behind a trusted domain. This cunning abuse allows the payload to pass through most DNS filters, firewalls, and antivirus tools undetected.
How It Works:
The script activates only during specific conditions, such as when the page includes the word “checkout” or when the browser isn’t automated.
Once triggered, it opens a WebSocket connection to a malicious server, allowing attackers to execute live, remote commands directly in the browser.
The payload is encoded and run using JavaScript’s Function constructor, enabling full control without triggering static scanners.
Why It’s Dangerous:
- No downloads or file execution are involved, just script execution within trusted browser sessions.
- Traditional antivirus, DNS filters, and CSPs are bypassed because the malware originates from Google.com, a domain rarely flagged.
- Even advanced endpoint protection may fail if it depends on domain reputation or doesn't analyse dynamic browser behaviour.
How to Stay Safe:
Avoid mixing personal and financial browsing sessions; use dedicated browsers or profiles for payments.
Limit third-party scripts using browser extensions or hardened settings (e.g., NoScript, uBlock Origin).
Be cautious of checkout pages behaving oddly, such as sudden slowdowns, popups, or redirects.
Use content inspection proxies or behavioural analytics if you're in an enterprise setting.
Encourage developers to implement strict Content Security Policies (CSPs) and scrutinise third-party integrations.
This attack underscores how trusted domains like Google can be exploited as delivery mechanisms, bypassing traditional defences and targeting the critical moment of online payment, right when users are least expecting it.
Cloudflare Blocks Record-Breaking 7.3 Tbps DDoS Attack in Just 45 Seconds
Cloudflare successfully mitigated the largest Distributed Denial-of-Service (DDoS) attack ever recorded. It stopped a 7.3 Tbps assault that delivered 37.4 terabytes of malicious traffic in just 45 seconds against an unnamed hosting provider using Cloudflare’s Magic Transit service.
Attack Highlights:
Occurred in mid-May 2025, surpassing the previous 6.3 Tbps record by 12%.
The scale of data was equivalent to streaming 9,350 HD movies or downloading over 12.5 million high-resolution photos in under a minute.
The attack targeted an average of 21,925 ports per second, peaking at 34,517 on a single IP address.
Originated from 122,145 unique IPs across 161 countries, leveraging 5,433 autonomous systems.
99% of the traffic consisted of UDP floods, with the rest being reflection and amplification attacks including:
QOTD and Echo reflection
NTP and RIPv1 amplification
Mirai-based UDP floods
Portmap floods
The intensity and concentration of the traffic, not just the volume, make this attack a serious evolution in DDoS strategies.
Geographic Distribution:
The largest traffic contributions came from Brazil and Vietnam, each responsible for about 25% of the malicious traffic, likely due to widespread exploitation of vulnerable IoT devices in emerging markets.
Mitigation Through Magic Transit:
Cloudflare’s Magic Transit service was the frontline defence. It provides cloud-based DDoS protection for on-premises, cloud, and hybrid networks. With a global mitigation capacity of 388 Tbps (23x the record attack), it operates without centralised scrubbing, by filtering traffic at the network edge.
This attack demonstrates the increasing power and coordination of modern botnets. While short in duration, the sheer intensity of 37.4 TB in 45 seconds represents a new class of high-impact DDoS events, requiring modern, distributed, and high-capacity defence systems like Cloudflare’s Magic Transit.
https://www.perplexity.ai/page/cloudflare-reports-fending-off-mQXKKeU2Qqmgt2dOUiI_Gg
Aflac Breach Highlights Ongoing Wave of Social Engineering Attacks on U.S. Insurers
Aflac, a leading supplemental insurance provider, confirmed a recent cyber attack involving unauthorised access to its network. This marked the third such disclosure by a U.S. insurance company within eight days. The breach occurred on June 12, 2025, and was swiftly contained, according to the company. While business operations remain unaffected and there is no evidence of ransomware, the investigation is ongoing.
Aflac joins Erie Insurance and Philadelphia Insurance Companies (a subsidiary of Tokio Marine) in reporting incidents between June 7 and June 12, all of which are believed to be part of a coordinated cyber crime campaign targeting the insurance sector.
The attack on Aflac is believed to have been carried out using social engineering tactics to trick staff into granting unauthorised access.
Potentially compromised data may include claims records, health information, Social Security numbers, and other personal information.
Aflac has not confirmed whether the attack was carried out by the threat group Scattered Spider, but the tactics are consistent with the group’s known methods.
“Given this actor’s history of focusing on a sector at a time, the insurance industry should be on high alert,” said John Hultquist, Chief Analyst at GTIG.
This recent string of attacks reflects a clear and organised threat pattern targeting insurers through non-technical vectors like social engineering. With multiple firms impacted in under a week, the insurance sector is being directly and actively targeted, and must urgently enhance employee training, access control, and incident response readiness.
https://cyberscoop.com/aflac-cyberattack-insurance-sector-scattered-spider/
Qantas Data Breach Exposes Millions of Customer Profiles Amid Airline Industry Cyber Threats
Qantas Airways has disclosed a cyber attack that compromised a third-party customer service platform, potentially affecting the personal data of up to six million individuals. The breach was detected on June 30, when the airline identified “unusual activity” in the system used by its contact centre.
Exposed Data:
Names
Email addresses
Phone numbers
Dates of birth
Frequent flyer numbers
However, no passwords, PINs, passport numbers, or financial information were compromised, and frequent flyer accounts remain secure, according to Qantas.
The company immediately contained the breach and is working to determine the full scope. While the total amount of stolen data is still being assessed, Qantas warns it expects the exposure to be “significant.”
Qantas has notified:
The Australian Federal Police
The Australian Cyber Security Centre
The Office of the Australian Information Commissioner
Qantas Group CEO Vanessa Hudson publicly apologised, acknowledging the concern caused. She reassured customers that airline operations and safety were not affected, whilst encouraging anyone with concerns to contact a dedicated support line.
https://www.bbc.com/news/articles/cd6gnyl9923o
Hackers Compromise Over 70 Microsoft Exchange Servers Using Stealth Keyloggers
A newly uncovered cyber campaign is targeting publicly exposed Microsoft Exchange servers with JavaScript-based keyloggers embedded directly into Outlook Web Access (OWA) login pages, according to researchers from Positive Technologies.
The attackers remain unidentified, but their tactics are stealthy and effective, designed to harvest credentials with minimal detection.
Key Details:
Two keylogger variants were identified:
Local keylogger: Stores stolen credentials in a file on the compromised Exchange server, which is remotely accessible.
Remote exfiltration keylogger: Sends data immediately to an external server using:
Telegram bot API via HTTP headers
DNS tunnelling combined with HTTPS POST requests
In some cases, attackers also collect cookies, browser User-Agent data, and timestamps for additional context.
Scope of the Campaign:
65+ victims in 26 countries, including government agencies, banks, IT companies, and educational institutions.
22 compromised servers belong to government entities/.
Countries most affected include Vietnam, Russia, Taiwan, China, Pakistan, Lebanon, Australia, Zambia, the Netherlands, and Turkey.
Attack Methodology:
The attackers exploit known vulnerabilities in Microsoft Exchange Server, especially ProxyLogon and ProxyShell bugs.
Known CVEs used in this campaign include:
CVE-2021-26855, 26857, 26858, 27065 (ProxyLogon)
CVE-2021-34473, 34523, 31207 (ProxyShell)
CVE-2020-0796, CVE-2014-4078, and others
Once access is gained, malicious code is injected into the login page, silently intercepting credentials as users authenticate.
Why It’s Dangerous:
Highly stealthy: Local keylogger variants do not generate outbound traffic, avoiding traditional detection.
Long-term persistence: Malicious scripts are embedded into legitimate web forms and can remain active for extended periods.
High-value targets: Government and enterprise sectors are being actively surveilled without alerting defenders.
Mitigation Recommendations:
Immediately patch Exchange servers against known CVEs
Audit login page source code for unauthorized JavaScript
Isolate Exchange servers from direct public exposure
Monitor for unexpected local file creations or unusual HTTP/S requests
Consider endpoint detection, DNS monitoring, and application-layer firewalls
https://thehackernews.com/2025/06/hackers-target-65-microsoft-exchange.html
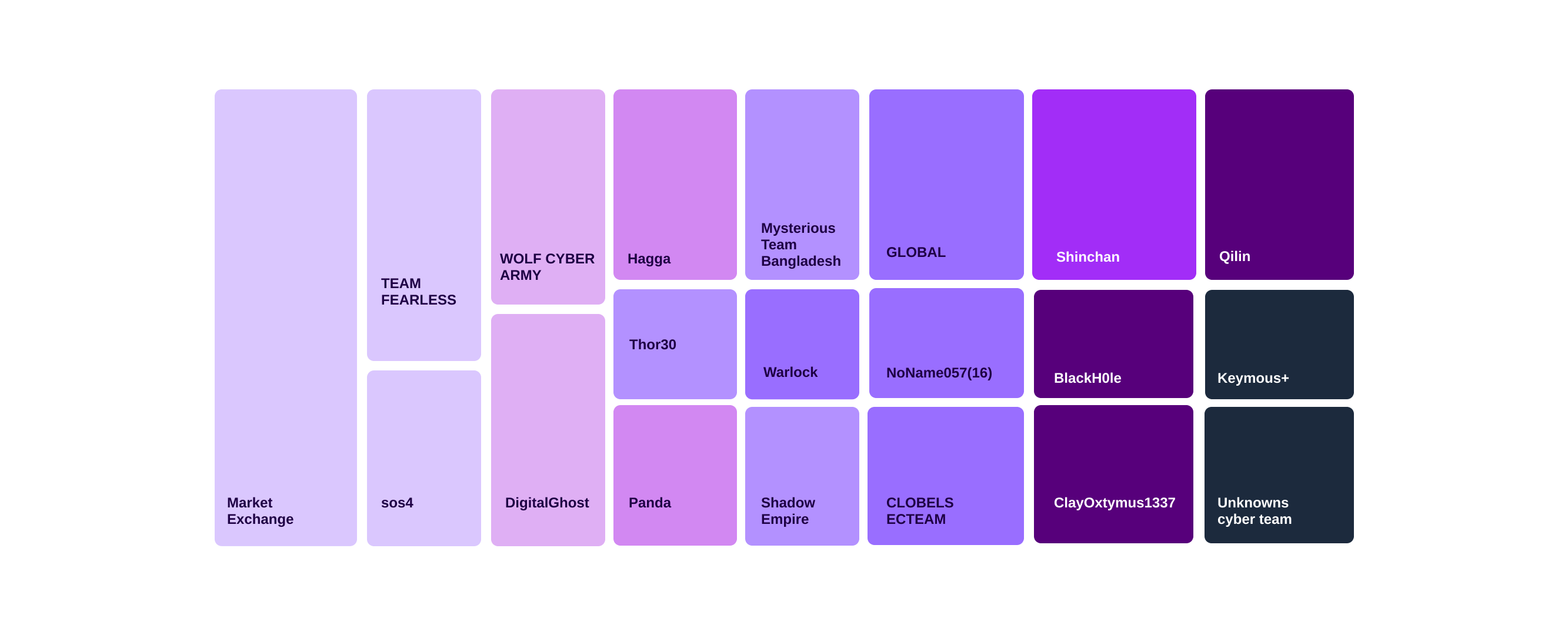
Threat actors targeting financial entities in June 2025
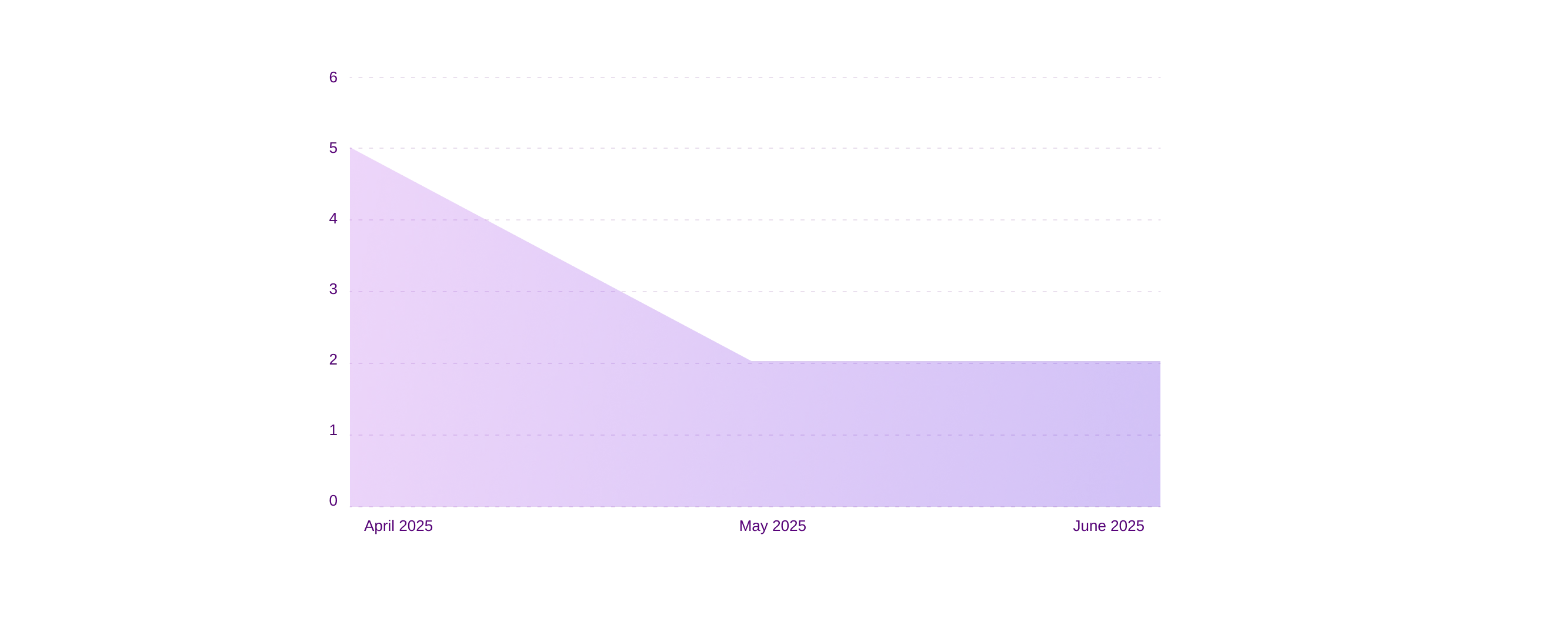
Ransomware vs Finance (last three months)

