Massive Aviation Data Leak: Everest Gang Claims 1.5M Dublin Airport Passenger Records
The Everest ransomware group recently made two significant new allegations, namely of a breach at Dublin Airport and an attack on Air Arabia. According to the group, they exfiltrated roughly 1,533,900 passenger records from Dublin Airport, and additional data belonging to around 18,000 Air Arabia employees.
Regarding the Dublin airport allegation, Everest claims that the stolen dataset includes highly sensitive travel and identity-related fields: full names, flight dates, passenger IDs, seat numbers, flight numbers, departure and destination airport codes, frequent-flyer details, baggage tag numbers, check-in device IDs, document forms and more. The group posted the victim listing on its dark web leak site and offered the stolen archive for US $1 million. The listing was password protected, meaning access to the full dataset has been restricted (for now). The airport itself has not yet publicly confirmed the incident in full, leaving some uncertainty about the claimed extent of the breach.


In parallel, Everest claims to have stolen employee records from Air Arabia, a UAE-based low-cost carrier. The group estimates there are 18,000 affected individuals and is offering that data for US $2 million. The exact nature of the data (whether full employee credentials or PII plus employment data) remains unspecified.
Everest has established itself as a prolific data-leak/ransomware actor since 2021, with hundreds of disclosed victims. Their recent pivot toward the aviation and travel sector may indicate a growing strategic focus on systems that contain highly sensitive traveller or operations data. For the aviation industry, the exposure of data such as device IDs, flight details and frequent-flyer status is particularly alarming, as it increases risks of identity theft, social-engineering attacks, targeted phishing, and supply chain manipulation. The fact that the header fields include boarding pass metadata and check-in device identifiers suggests the attackers gained deeper access than just a simple customer database leak.
https://hackread.com/everest-ransomware-dublin-airport-passenger-data/
EY Exposes 4 TB SQL Backup to the Internet, Revealing Credentials and Tokens
A recent data exposure involving Ernst & Young (EY) has drawn significant attention after a Dutch cybersecurity research firm discovered that the company had inadvertently left a 4-terabyte SQL Server backup publicly accessible online. The unencrypted file, stored in a misconfigured cloud bucket, contained an extensive volume of sensitive information, including API keys, cached authentication tokens, service account passwords, and user credentials, effectively granting anyone who accessed it the digital equivalent of EY’s internal “master keys.”
The incident, reported on 29 October, 2025, appears to stem from a common yet critical misconfiguration: cloud storage left open to public access without encryption or authentication. Researchers identified the exposed file after scanning open cloud repositories and confirmed its contents by retrieving a small sample of the data. Although the exact duration of the exposure remains unknown, indicators suggest the file was accessible for a considerable period of time before discovery, potentially allowing automated bots or malicious actors to locate and copy it.
After the researcher privately notified EY through LinkedIn and other channels, the firm reportedly secured the exposed system within a week. Nevertheless, the scale and sensitivity of the leaked data raise serious concerns. This represents an enormous attack surface, one that could allow threat actors to move laterally across EY’s internal systems or exploit trust relationships with clients and partners.
Given EY’s extensive role as a service provider to multinational corporations, including those in financial services, the potential for downstream compromise is considerable. Attackers armed with exposed credentials could leverage them to gain access to client environments, exploit third-party integrations, or impersonate trusted systems within interconnected supply chains. Beyond the technical risk, the incident carries regulatory and reputational implications for EY and its customers, who may now question the firm’s security posture and data-handling practices. This exposure highlights several recurring problems in corporate cybersecurity. Misconfigured cloud storage remains one of the most frequent causes of large-scale data leaks, often affecting even the most security-mature organisations.
While EY hasn’t publicly disclosed the full details or potential impact, the exposure is a cautionary example of how easily human error in cloud configuration can lead to enterprise-wide compromise. For large organisations and their clients alike, it reinforces the growing need for proactive data governance, continuous validation of third-party controls, and rapid response capabilities when digital trust is at stake.
https://www.theregister.com/2025/10/29/ey_exposes_4tb_sql_database/
Capita Hit with £14 Million Fine Over Huge 2023 Pension-Admin Data Breach
In October 2025, the UK Information Commissioner’s Office announced that Capita had been fined £14 million after a cyberattack in March 2023 exposed the personal data of approximately 6.6 million people. The fine was split between Capita plc (£8 million) and its subsidiary, Capita Pension Solutions (£6 million).
The breach had a broad impact: it affected 325 of the more than 600 organisations that used Capita’s pension and outsourcing services, covering sensitive data, ranging from pension scheme records, to detailed personal and financial information. The ICO’s investigation revealed a sequence of critical failures. Although the intrusion began with the download of a malicious JavaScript file on 22 March 2023, Capita didn’t quarantine the compromised device until 58 hours later, despite its internal target of responding within one hour.
During this window, attackers installed Qakbot malware and Cobalt Strike tooling, escalated privileges via a backup admin account, with domain admin rights, moved laterally across Capita’s network into multiple domains, and exfiltrated nearly one terabyte of data. The ICO also found that, prior to the attack, Capita had been repeatedly warned, via three separate penetration tests, about the risks of its administrative account structure, and was operating with an understaffed Security Operations Centre that consistently failed to meet its SLA targets. Capita initially faced a proposed fine of £45 million, but the amount was reduced after the company demonstrated post-incident improvements, cooperated with regulators, including the UK’s National Cyber Security Centre, and offered remediation support to affected individuals.
For organisations in regulated sectors, particularly financial services, this incident highlights clear risk lessons: outsourcing to large service providers does not remove your exposure; insufficient privilege segmentation and delayed response to alerts can dramatically amplify impact; and legacy or misconfigured admin accounts, remain one of the most reliable attack vectors for adversaries.
https://www.theregister.com/2025/10/15/ico_fines_capita_14m/
Renault Group UK Warns of Third-Party Processor Breach Exposing Customer Records
Renault Group UK recently notified its customers that their personal information may have been compromised following a cyberattack targeting one of its third-party data processing providers. While Renault emphasised that its own internal systems were not breached, the incident nonetheless raises significant supply chain risk concerns for customers and vendors alike.
According to the notification, the exposed data may include full names, phone numbers, email addresses, postal addresses, genders, vehicle registration numbers and vehicle identification numbers (VINs). Renault clarified that no banking or financial account details were reported as compromised in this incident.
The breach appears to stem from the vendor, not Renault’s direct infrastructure, and the company states that the incident was contained, that it is cooperating with the third-party provider, and that affected customers are being notified and warned to remain vigilant against phishing and unsolicited requests for information.
This breach fits into a broader trend of automakers and their supply chains coming under increased cyber threat pressure. With attackers moving beyond direct intrusion into manufacturing or operations, this event underscores the growing strategic emphasis on trusted vendor networks and peripheral data assets such as vehicle and customer records.
From a risk perspective, even though financial details weren’t exposed, the compromised data (especially VINs and registration numbers) can be leveraged for social engineering, identity theft, targeted phishing, or even fraudulent access to connected vehicle services. The fact that the third-party service provider, rather than Renault itself was the vector, should remind organisations, especially in regulated sectors like finance, that vendor ecosystems must be treated as potential threat entry points.
https://hackread.com/renault-uk-customers-third-party-data-breach/
SonicWall Cloud Backup Breach: Firewall Configs Exposed for All Customers
In mid-September 2025, SonicWall disclosed a major security incident involving its “MySonicWall” cloud backup service, in which threat actors accessed customer firewall configuration backup files stored in the cloud. While the vendor originally stated that fewer than 5% of its users were impacted, a subsequent investigation with Mandiant revealed that all customers who used the cloud backup feature were affected.
The backups contained sensitive configuration files (with extension .EXP) including network rules, VPN definitions, authentication credentials, remote access settings, and other device-preference data. Although the credentials remained encrypted (with older devices using weaker 3DES, and newer “Gen 7” devices using AES), the fact that adversaries now hold full configuration snapshots means they can map network topology, identify inbound services, and potentially launch targeted attacks using that intelligence.
The breach began when attackers executed a brute-force attack against the MySonicWall cloud-backup API; using the acquired credentials and access paths, they accessed the stored backups. Initially the event was downplayed (under 5% were impacted), but in early October 2025, SonicWall updated its advisory: 100% of cloud-backup customers were impacted.
Though SonicWall affirmed that its firmware, code base and other product components were not compromised, the downstream risk is substantial. Customers with impacted backups must assume their firewall credentials and configurations might be known to adversaries, increasing their vulnerability to follow-on intrusion or network reconnaissance.
This incident serves as a harsh reminder that even security vendors and appliance providers are not immune from vendor risk and supply chain style exposures. Firms that outsource device management, rely on cloud configuration backups, or maintain remote admin/management consoles, must treat vendor backups as part of their own attack surface. Delays in resetting credentials, overlooking backup encryption or credential reuse across appliances, and insufficient segmentation of cloud management portals, can turn an appliance vendor breach into a full corporate compromise.
https://hackread.com/sonicwall-hackers-breached-all-firewall-backups/
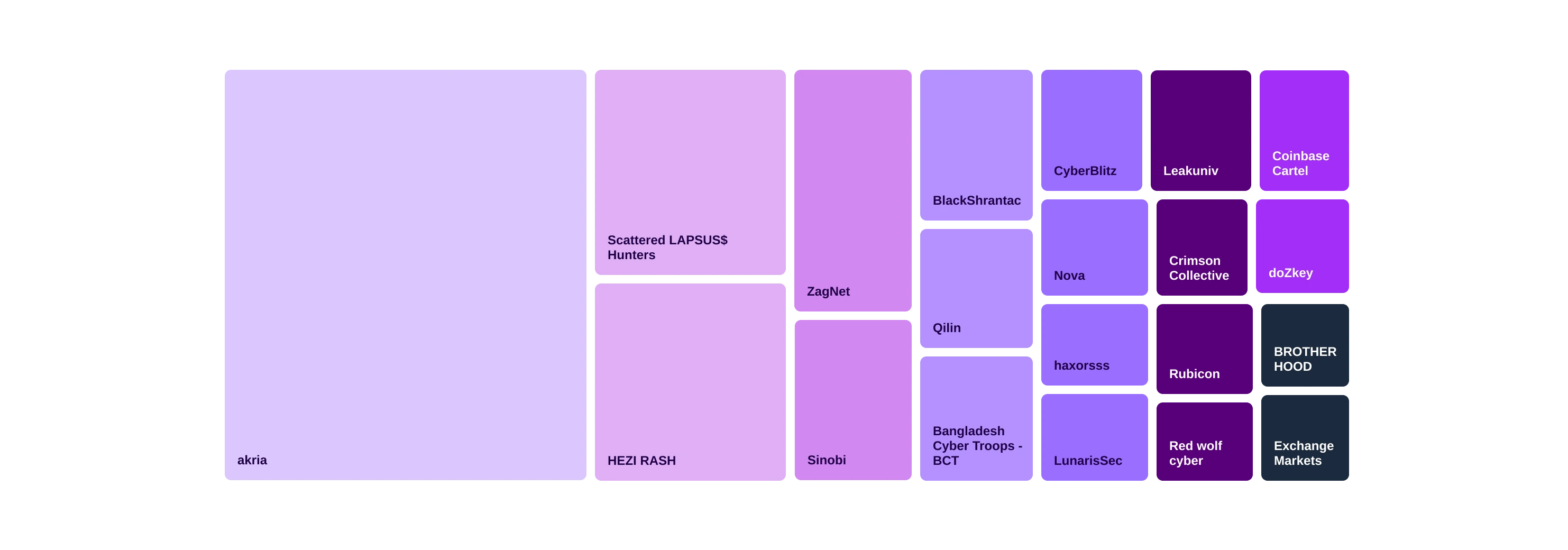
Threat actors targeting financial entities in October 2025
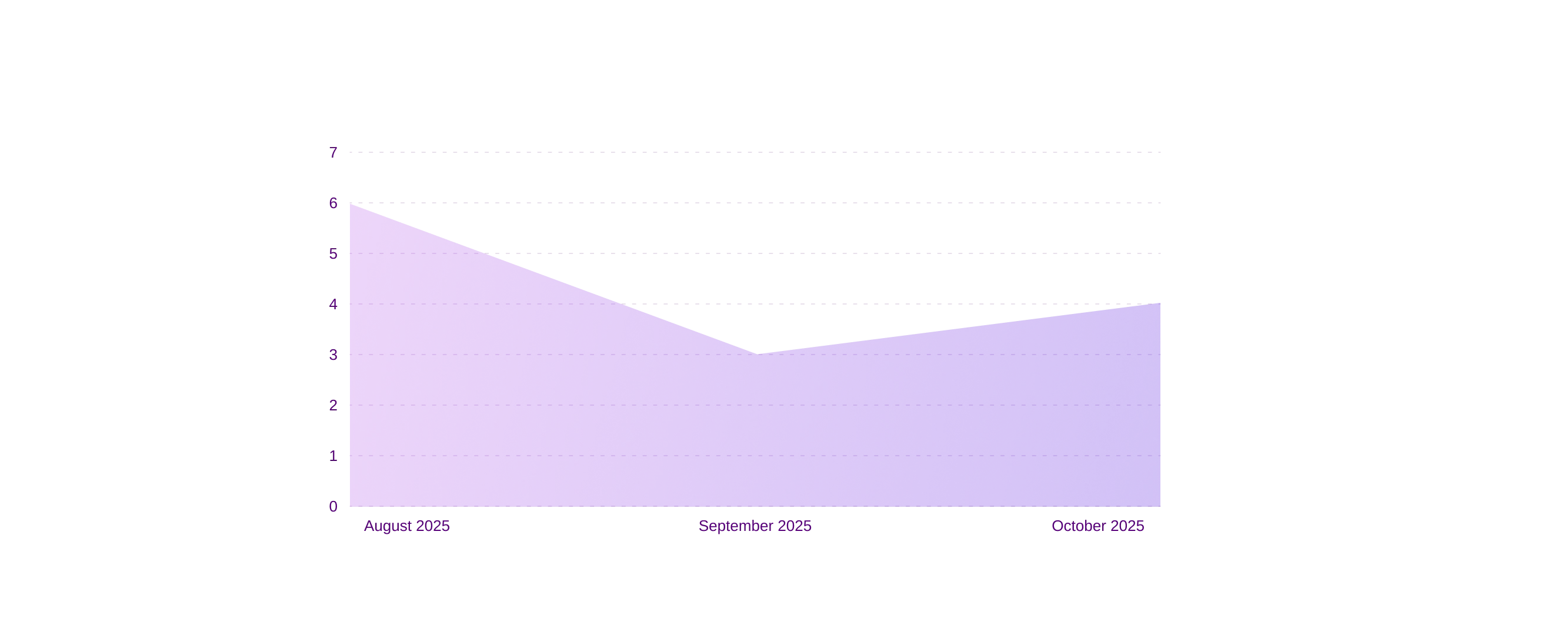
Ransomware vs Finance (last three months)

Managing Risk of AI Adoption
AI is transforming how organisations across the globe work, from powering internal knowledge hubs and embedding tools like CoPilot in Teams, to generating production-ready code. But every innovation brings new cyber risks, compliance challenges, and attack surfaces. By utilising our AI code testing service, you can ensure your AI deployments are resilient, compliant, and ready for the real world.

