Ransomware Attack Cripples Polish Hospitals, Raising Concerns Over Critical Infrastructure Security
A major wave of ransomware attacks has struck hospital systems and municipal water infrastructure across Poland, disrupting patient care and critical services. The incidents have been attributed by officials to cyber groups operating with ties to Russian influence.
Hospitals in several regions suffered operational disruptions: some were forced to revert to paper-based processes, delay non-emergency procedures, or divert patients. Information systems and internal networks experienced outages, limiting access to digital health records, scheduling systems, and other hospital IT services. In many cases, hospital staff had to resort to manual workflows for diagnostics, recordkeeping, and patient communication.


The attacks are not isolated to health care. Local water utility infrastructure also came under siege, compounding public safety risks by threatening water supply and the integrity of municipal systems.
Authorities and specialists suggest that the threat actors aim to maximise disruption and pressure by hitting highly vulnerable targets. The use of ransomware in this manner underscores how critical service providers are being viewed as strategic targets. In response, Poland’s cybersecurity agencies and national incident response teams are actively engaged, working to contain the damage, restore services, and coordinate with hospitals to resume operations.
This pattern of targeting underscores a growing trend: state-aligned or heavily resourced cyber actors are weaponising operational technology, public infrastructure, and essential services to cause social disruption and exert geopolitical pressure.
Finally, it's important to highlight the urgent need for continuous cyber resilience, robust incident response planning, and cross-sector collaboration. It makes clear that entities operating in health, utilities, and other critical sectors must invest in proactive defences, monitoring tools, and recovery capabilities—not just reactive measures.
https://www.teiss.co.uk/news/ransomware-disrupts-polands-hospital-operations-and-patient-care-16411
North Korea’s Kimsuky Leverages AI-generated Military ID Deepfakes in Targeted Phishing Campaign
North Korea–linked APT Kimsuky has shifted tactics and launched a phishing campaign that uses AI-generated fake military ID cards as social-engineering bait to trick recipients into executing malicious files. The campaign was detected in July 2025 by Genians Security Center (GSC), which reported that the attackers sent emails impersonating a legitimate South Korean defence institution and attached a ZIP file that appeared to contain a draft military ID.
The image on the purported ID is not a real photograph but a deepfake produced with AI tools; GSC’s analysis indicated the portrait had a 98% certainty of being AI-generated. When victims open the attachment, a hidden malicious program runs: the malware waits a few seconds and then downloads a payload (identified as LhUdPC3G.bat ) from a remote server. The attack uses both batch files and AutoIt scripts to establish persistence.
To persist and evade detection, the attackers create a scheduled task named HncAutoUpdateTaskMachine that executes every seven minutes and is disguised as an update for Hancom Office.
This operation represents an evolution from Kimsuky’s earlier “ClickFix” approach, which relied on fake security pop-ups to trick victims into running commands, toward more convincing, AI-enabled decoys designed to increase click-through and reduce user suspicion. The use of AI-generated images demonstrates how readily available generative tools can be weaponised to create highly believable lures.
It is important to note that this is not an isolated misuse of generative AI: other state-linked groups have also abused AI to fabricate identities or otherwise support attacks (for example, creating fake profiles to pass technical interviews). Given the obfuscated script techniques used in these emails, security vendors emphasize the need for Endpoint Detection and Response (EDR) solutions and robust detection controls to spot script-based activity and block payload downloads before they execute.
In short, the campaign shows three concerning trends for defenders:
- increasing sophistication of social engineering using AI deepfakes,
- reuse of automation and persistence mechanisms across campaigns,
- the attacker preference for stealthy script-based loaders that delay actions to evade simple static detection.
The recommended mitigations are layered: user awareness and phishing-resistant authentication; EDR and script-blocking controls; network egress filtering to stop malicious downloads; and proactive hunting for scheduling tasks and anomalous startup entries that mimic legitimate update mechanisms.
https://hackread.com/north-korea-kimsuky-group-ai-generated-military-ids/
Cyberattack on Aviation Software Cripples Heathrow and European Airports, Causing Major Delays
A large-scale cyberattack targeting a critical aviation software provider disrupted operations at multiple major European airports, including London Heathrow, Brussels, and Berlin, causing hundreds of flight delays and cancellations.
The root cause was a failure in Collins Aerospace’s “Muse” system, a software platform used by many airlines to share check-in desks, boarding gates, and baggage systems. That software was rendered inoperable, disabling electronic check-in and baggage drop systems at affected airports.
In response, airports had to disconnect from the affected systems and switch to manual processing of passenger check-ins, boarding, and baggage handling. This shift overwhelmed staff created long queues and significantly slowed operations.
At Heathrow’s Terminal 4, travellers reported waiting more than two hours in queues. In many cases, mobile boarding passes failed, and staff had to resort to tagging luggage and processing check-ins by hand or via phone.
Brussels Airport confirmed the attack occurred Friday night and led to a large impact on flight schedules, multiple delays, and at least 10 flight cancellations. Berlin’s Brandenburg Airport also suffered extended waiting times. Outside those major hubs, Dublin and Cork airports in Ireland experienced lesser, but still noticeable impact, with some carriers switching to manual check-in procedures.
RTX (formerly Raytheon Technologies), the parent company of Collins Aerospace, acknowledged the cyberattack affecting “select airports.” They clarified that the disruption was limited to “electronic customer check-in and baggage drop” systems. RTX claimed mitigation via manual fallback procedures and assured that their teams were actively working to restore full functionality.
Affected airports deployed extra staff to help manage the backlog and advised passengers to check flight status with their airlines before traveling to the airport to avoid unnecessary delays. According to flight tracking service FlightAware, hundreds of flights across the impacted airports were delayed on that Saturday. For Brussels alone, 10 flights were cancelled, and 17 flights were delayed by more than one hour.
https://cybersecuritynews.com/heathrow-european-airports-cyberattack/
Jaguar Land Rover Cyberattack Exposes Costly Gap in Cyber Insurance and Supply Chain Resilience
Jaguar Land Rover (JLR), the British luxury automaker owned by Tata Motors, suffered a major cyberattack in early September 2025 that disrupted its global production and sales operations. The company was forced to shut down its IT systems across manufacturing and retail networks as a containment measure, halting production at its UK plants and affecting tens of thousands of employees. Dealers were only able to sell vehicles already in stock, as systems for registering new cars were rendered unavailable. Although JLR stated that some data might have been affected, it did not confirm whether customer or employee information was compromised. The incident extended across JLR’s supply chain, with smaller suppliers facing financial stress due to suspended production and delayed payments. Analysts suggested that the breach could be linked to known threat groups and might have exploited vulnerabilities in enterprise software such as SAP, highlighting weaknesses in supply chain security and digital infrastructure. A particularly striking element of this case is that JLR had been negotiating a cyber insurance policy before the attack occurred, but had not completed the purchase. This left the company without coverage for cyber-related damages, including business interruption losses, data restoration costs, and reputational impact. The absence of insurance significantly magnified the financial and operational consequences of the incident, forcing JLR to absorb all associated costs internally. This situation illustrates the critical importance of timely insurance placement, as even brief gaps in coverage can expose large enterprises to substantial unmitigated losses.
The event also underscored broader issues in cyber risk management for industrial organisations, where interconnected IT and operational technology systems increase exposure. Insurers are likely to use JLR’s experience as a case study for tightening underwriting requirements, emphasising continuous patching, vendor risk oversight, network segmentation, and incident response maturity. The attack’s cascading effect through JLR’s supply chain demonstrated that the most severe financial losses often stem not from direct ransom demands but from extended business disruption and partner dependencies.
Overall, the JLR cyberattack serves as a reminder that even technologically advanced firms are vulnerable when cyber resilience and insurance strategies are not fully aligned. The case highlights how a delayed policy finalisation can turn an operational crisis into a multi-million-pound financial burden and reinforces the growing need for both manufacturers and insurers to reassess how they measure and mitigate systemic cyber risks across industrial sectors.
https://hackread.com/jaguar-land-rover-cyberattack-disrupts-operations/
Attacker Automates Malware Delivery Using Claude AI Agents to Scale Phishing Campaigns
Jagged, fast-moving phishing activity described in the Cyber Express piece shows a threat actor using Anthropic’s Claude (an AI agent) to automate multiple stages of an email-based attack chain, from crafting convincing lures to generating payload-delivery scripts, so the human operator can scale operations with minimal hands-on effort.
According to the report, the attacker used Claude to generate a sequence of actions that included producing social-engineering content, building archive files that appear legitimate, and assembling AutoIt/batch script loaders that fetch and execute the real malware. By delegating repetitive authoring and scripting tasks to an AI agent, the actor shortened the development cycle and reduced the skill threshold required to run complex campaigns.
The automation also improves operational security for the attacker: AI-generated text and artefacts can be rapidly tweaked to evade static detection or to tailor lures to different targets, while the scripts incorporate simple evasive techniques (delays, process hiding, disguised task names) to increase the chance of successful execution after a user opens an attachment. The article notes that this pattern shifts the defender’s problem from “can we detect this single lure?” to “how do we detect entire classes of AI-assisted, script-based loaders?”
From a defender perspective the piece highlights several practical mitigations: enforcing strict script-execution policies (blocking AutoIt/batch when not required), using EDR to detect script behaviours and scheduled tasks, filtering and sandboxing email attachments, applying egress filtering to prevent staged payload downloads, and bolstering phishing awareness training with examples of AI-crafted lures. These controls aim to interrupt the automated chain at multiple points rather than relying on single-point signature detection.
The report underscores a wider trend: readily available generative AI tools are being weaponised not only to improve the believability of phishing content but to automate the operational plumbing of attacks. This lowers the bar for less-skilled attackers and increases campaign velocity, meaning organisations must adopt layered defences and assume that future phishing waves will be both higher-volume and more contextually convincing.
https://thecyberexpress.com/hacker-used-claude-ai-to-automate-attack/
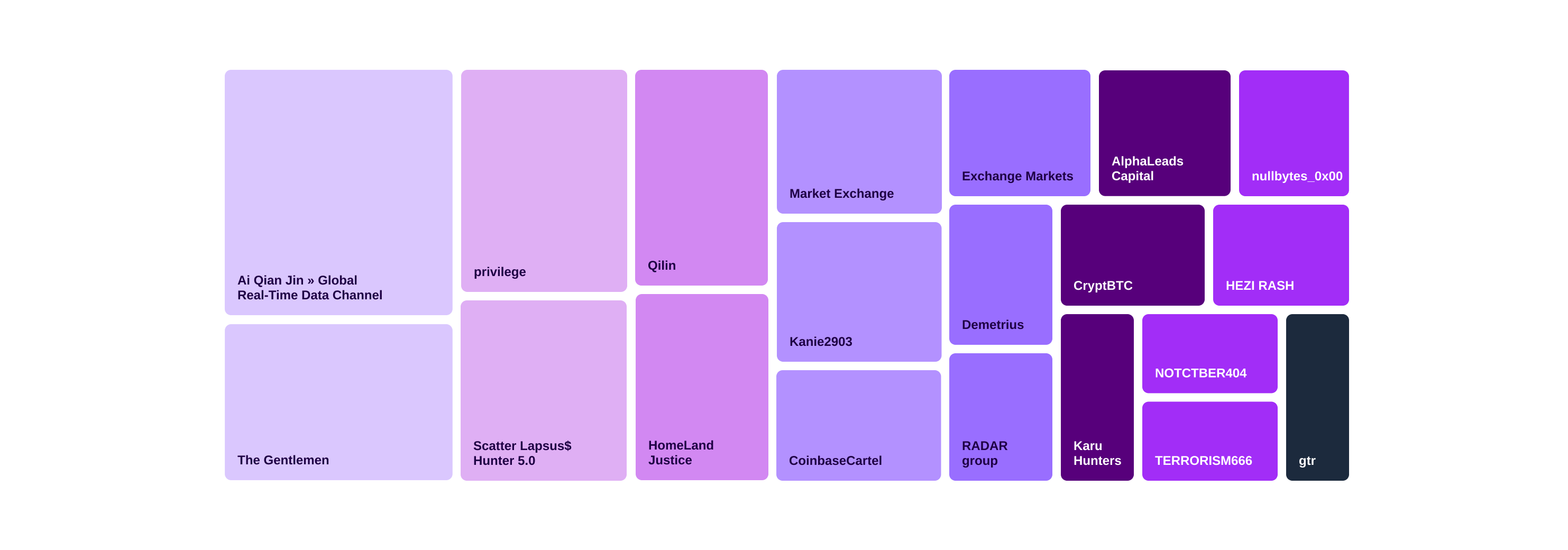
Threat actors targeting financial entities in September 2025
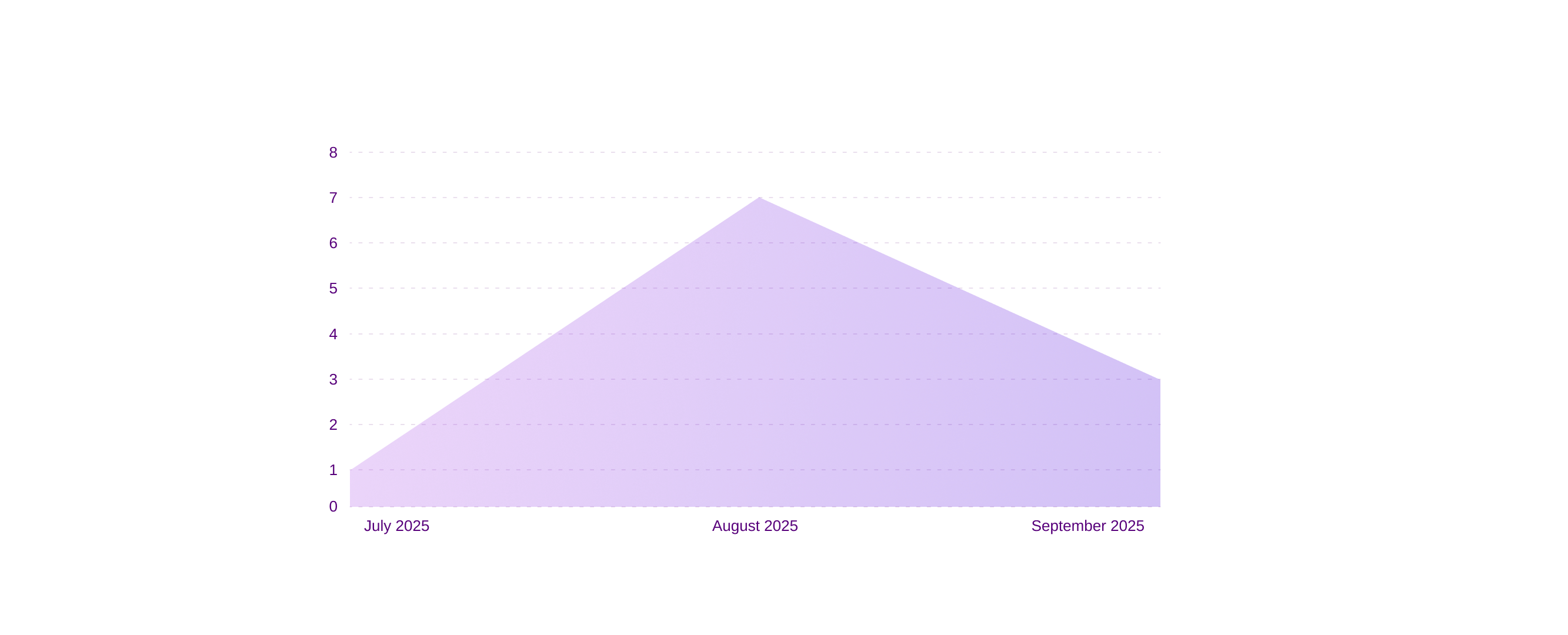
Ransomware vs Finance (last three months)

Managing Risk of AI Adoption
AI is transforming how organisations across the globe work, from powering internal knowledge hubs and embedding tools like CoPilot in Teams, to generating production-ready code. But every innovation brings new cyber risks, compliance challenges, and attack surfaces. By utilising our AI code testing service, you can ensure your AI deployments are resilient, compliant, and ready for the real world.

